Category: Data Security
-

Game-Changing Technology Trends Shaping 2026
By 2026, artificial intelligence and emerging tech are on track to automate up to 70% of everyday tasks, fundamentally transforming how we live, work, and interact with machines. The following 17 trends are not just futuristic predictions—they’re already unfolding before our eyes.
-

Unlocking the Power of Docling — From Chaos to Context in AI
Docling bridges the gap between chaotic real-world documents and structured AI-ready data. Whether you’re building search tools, RAG systems, or intelligent content ingestion pipelines, this open-source toolkit offers accuracy, speed, and community-backed innovation. If you’re eager to tame your document chaos, Docling may just be your next AI ally
-
AI Products to Build in 2025
Manu Arora paints an inspiring yet grounded roadmap for AI startup builders in 2025. Whether you’re passionate about education, productivity, creativity, or health, there’s a unique opportunity to create powerful, niche AI solutions. The future belongs to those who combine creative domain insight with smart AI integration.
-

Keeping APIs Up During Peak Loads
Ensuring API uptime during peak loads isn’t a one-time setup—it’s a continuous practice. From planning load tests and configuring auto-scaling to adding caching and resilience patterns, every piece plays a role. Pair these best practices with effective monitoring and degradation strategies to keep your API responsive, reliable, and user-friendly, even when traffic spikes unexpectedly.
-

Unstr: Automate Unstructured Data Processing with AI
Unstr is highlighted as a useful tool for organizations managing high volumes of data and needing reliable document parsing. The video encourages viewers to explore the platform for streamlining unstructured data processing.
-

The $1 SUV: How Prompt Injection Can Hijack Your AI Systems
Chatbots powered by Large Language Models (LLMs) are becoming increasingly common, offering convenient and engaging ways to interact with technology. However, as IBM Distinguished Engineer Jeff Crume explains in a recent video, these systems are vulnerable to a unique type of cyberattack called prompt injection. This post delves into the details of prompt injection, its potential…
-
Safeguard Your Chatbots with Garak: Identifying LLM Vulnerabilities
LLMs can be vulnerable to various attacks, including prompt injection, data leakage, and even generating malicious code. But how do you proactively test your LLM-powered applications for these weaknesses? Enter Garak, an open-source LLM vulnerability scanner. In this blog post, I’ll break down the key takeaways from the video and show you how to use…
-

The One-Line Hack: How XSS Attacks Compromise Your Security
Cross-site scripting (XSS) attacks are a type of cyber threat where hackers inject malicious scripts into trusted websites. These attacks can compromise user data, including sensitive information like cookies and session tokens, often with just a single line of code. Here’s a breakdown of how XSS attacks work and their types. What is Cross-Site Scripting…
-
Load Balancers are not Magic – Dissecting Atlassian Outage
The Atlassian outage serves as a valuable lesson. While load balancers are powerful tools, they are not a panacea for all system failures. By implementing a comprehensive approach that includes robust monitoring, redundancy, and proactive testing, organizations can build more resilient systems that can withstand unexpected challenges.
-
Turn ANY Website into LLM Knowledge in SECONDS
Crawl for AI is a revolutionary tool that empowers you to transform any website into valuable knowledge for your LLMs. Its speed, efficiency, and user-friendly interface make it an indispensable asset for anyone seeking to enhance the capabilities of their LLMs. By leveraging Crawl for AI, you can unlock the full potential of LLMs and…
-
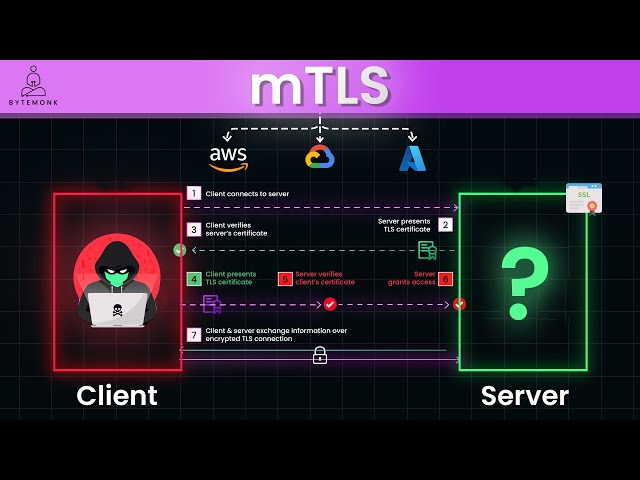
mTLS: Securing Your Microservices from MITM Attacks
Understanding mTLS Mutual Transport Layer Security (mTLS) is a robust security protocol that ensures two-way authentication and encryption between communicating parties. It’s an extension of the standard TLS protocol, which is widely used to secure internet traffic. How mTLS Works Benefits of mTLS Implementing mTLS in Microservices Best Practices
-

Microsoft Ignite 2024: Everything Revealed in 15 Minutes
Microsoft Ignite 2024 showcased the company’s commitment to innovation and its vision for the future of technology. With a strong focus on AI, security, and cloud computing, Microsoft is well-positioned to help organizations navigate the digital landscape.